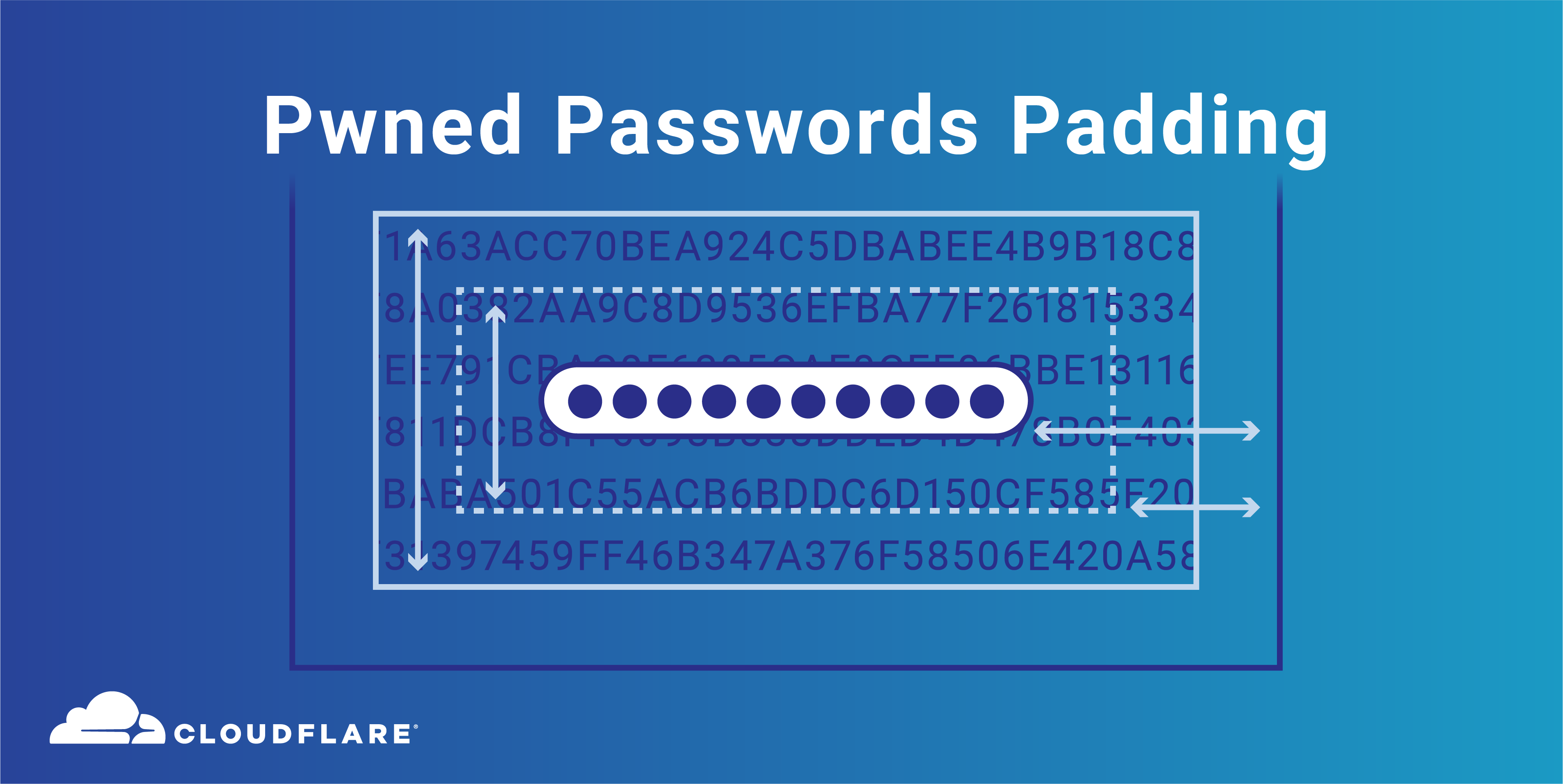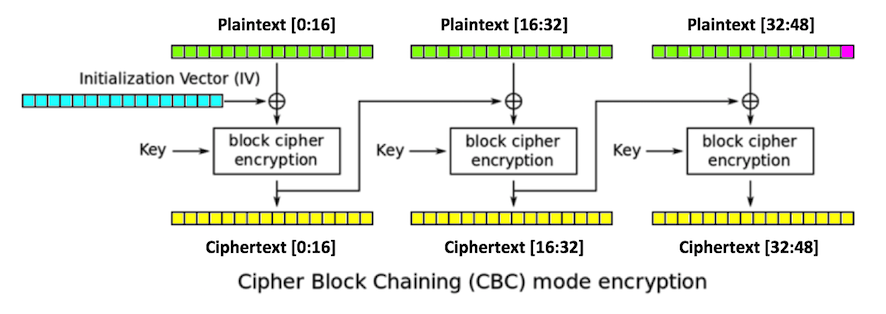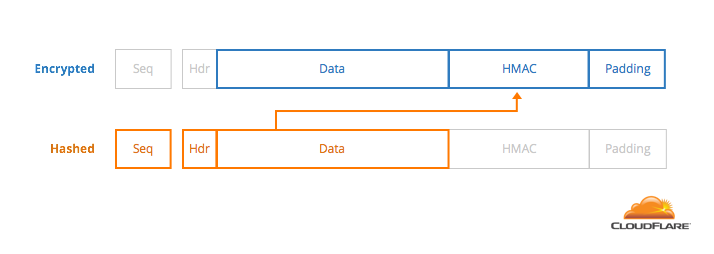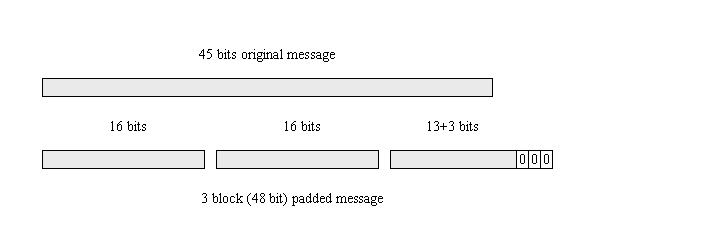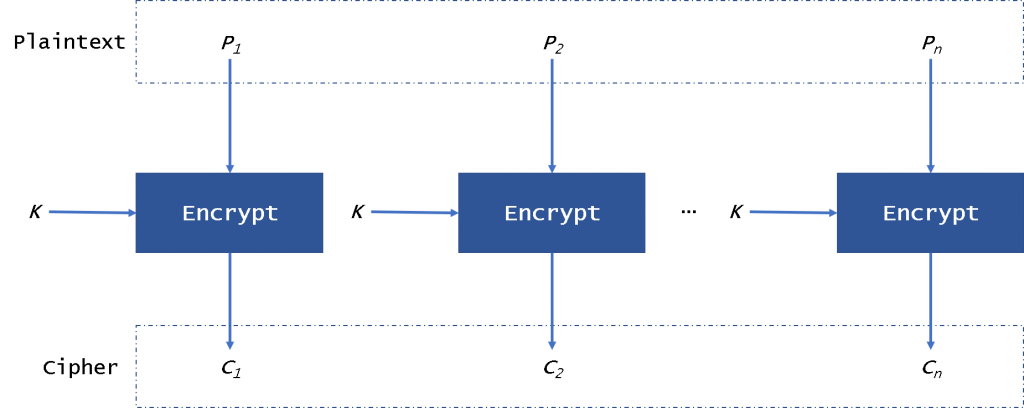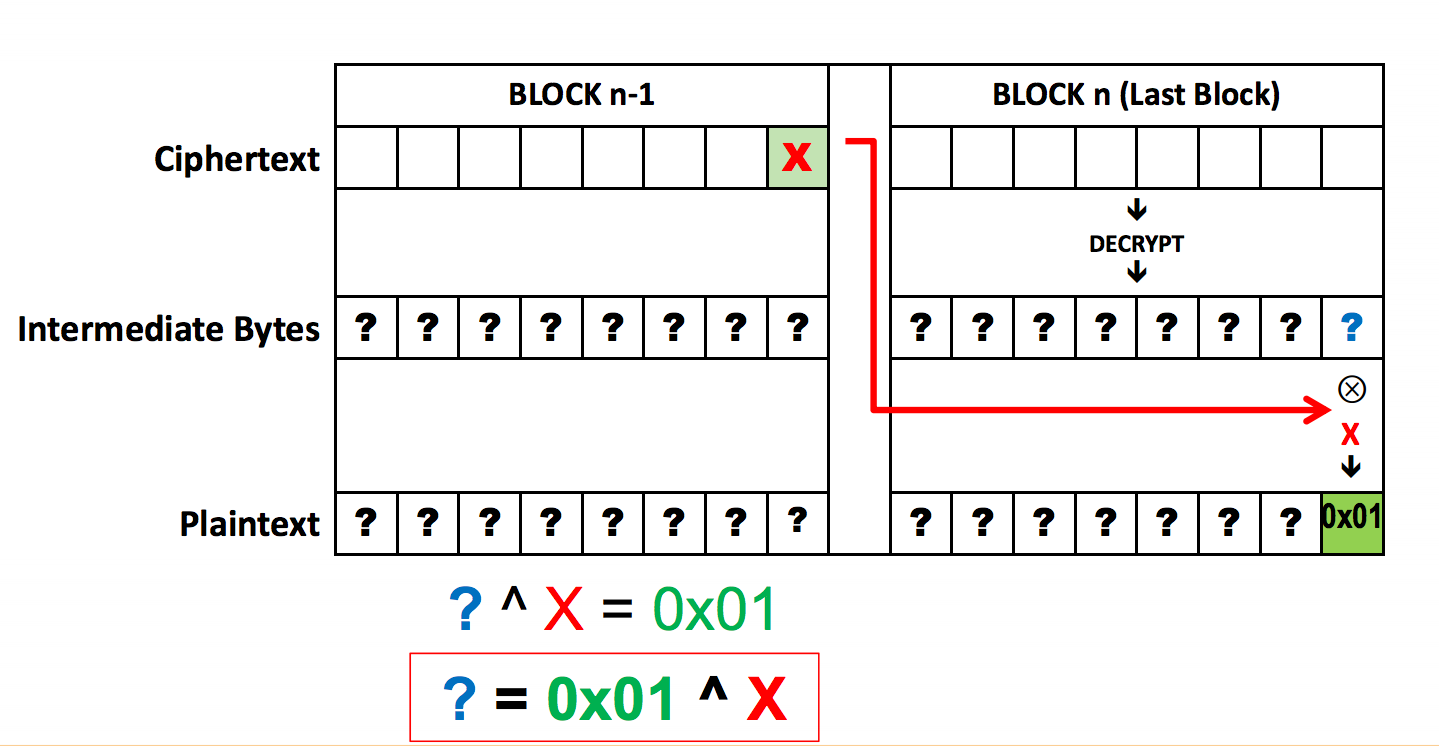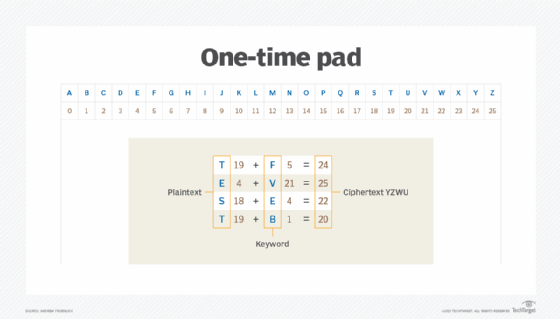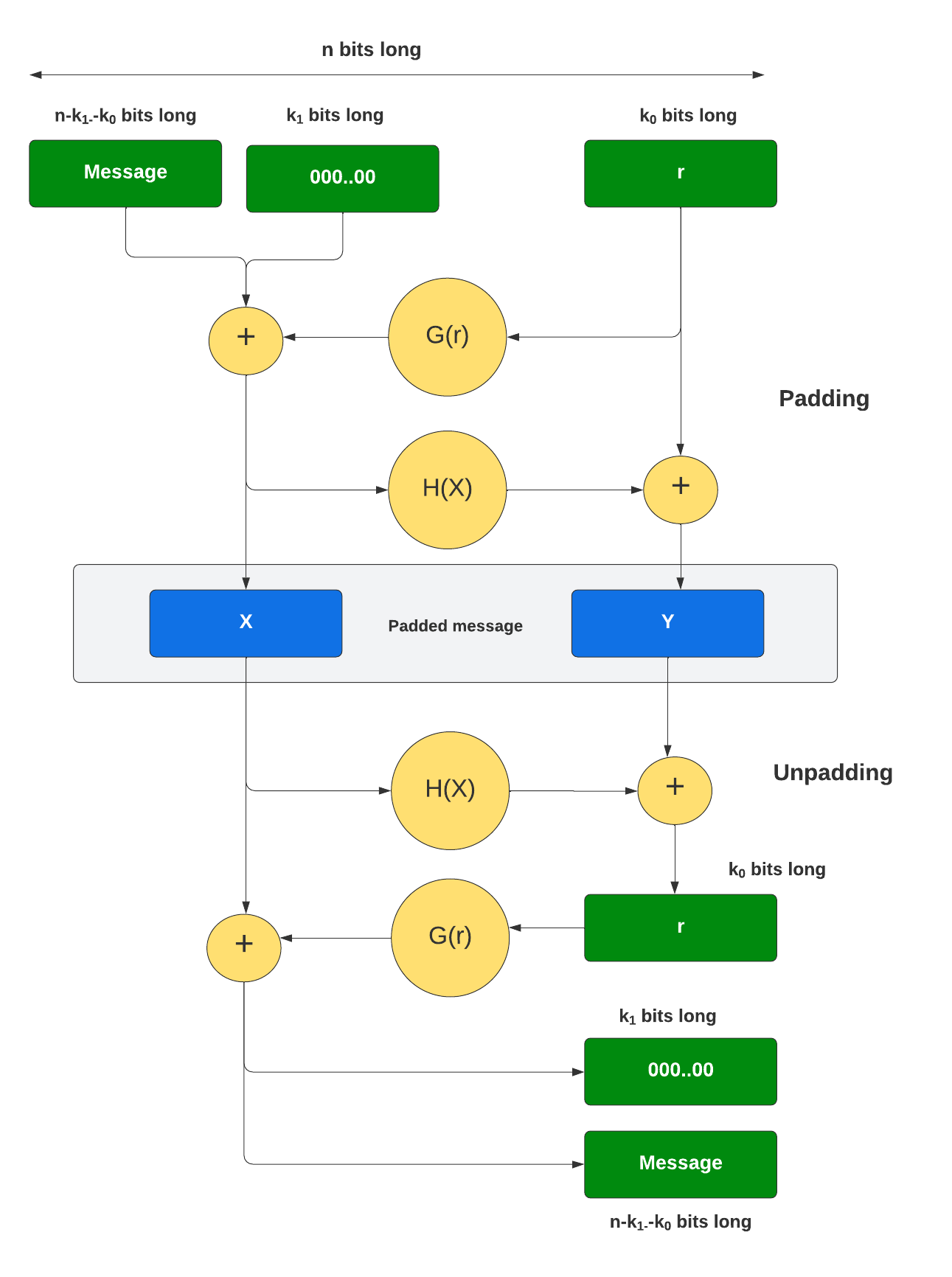
So How Does Padding Work in RSA?. Basically, PKCS#v1.5 is bad, OAEP is… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

rsa - Why PS does differ between PKCS1 v1.5 padding for signature and for encryption? - Cryptography Stack Exchange

Session-Based Random Selection Padding Scheme with Elliptic Curve Cryptography for Web Service Security Development | SpringerLink

Wonk post: chosen ciphertext security in public-key encryption (Part 2) – A Few Thoughts on Cryptographic Engineering
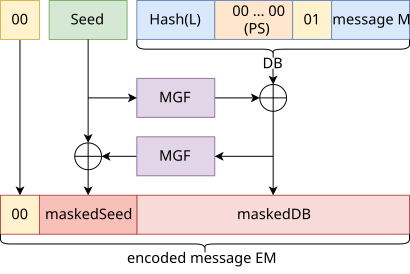
![PDF] Practical Padding Oracle Attacks | Semantic Scholar PDF] Practical Padding Oracle Attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4edcfb956fe22ef22c95076ce1003e6d85d4ad32/7-Figure2-1.png)