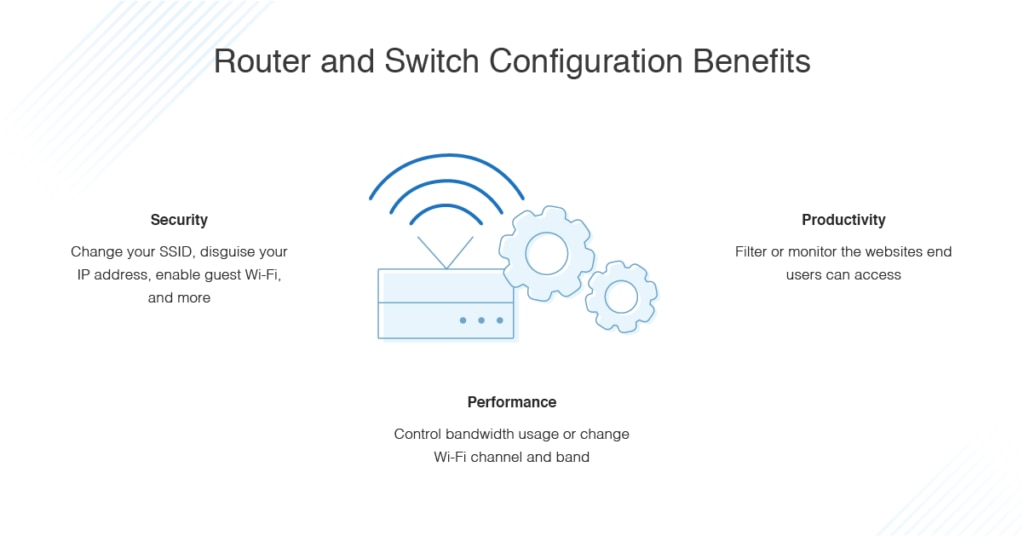
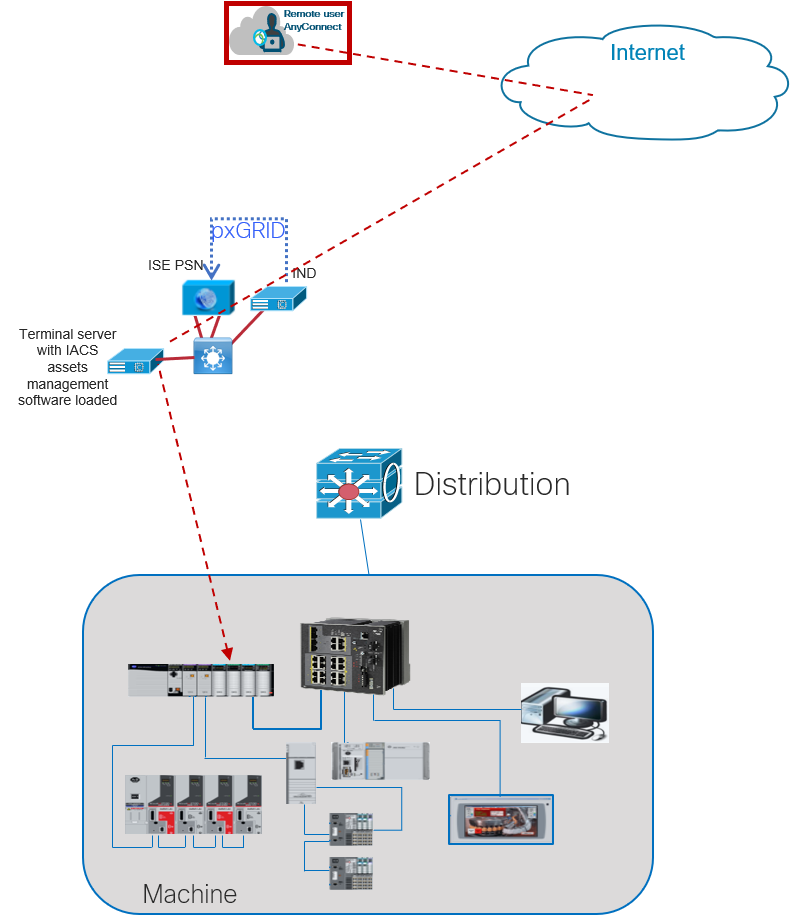
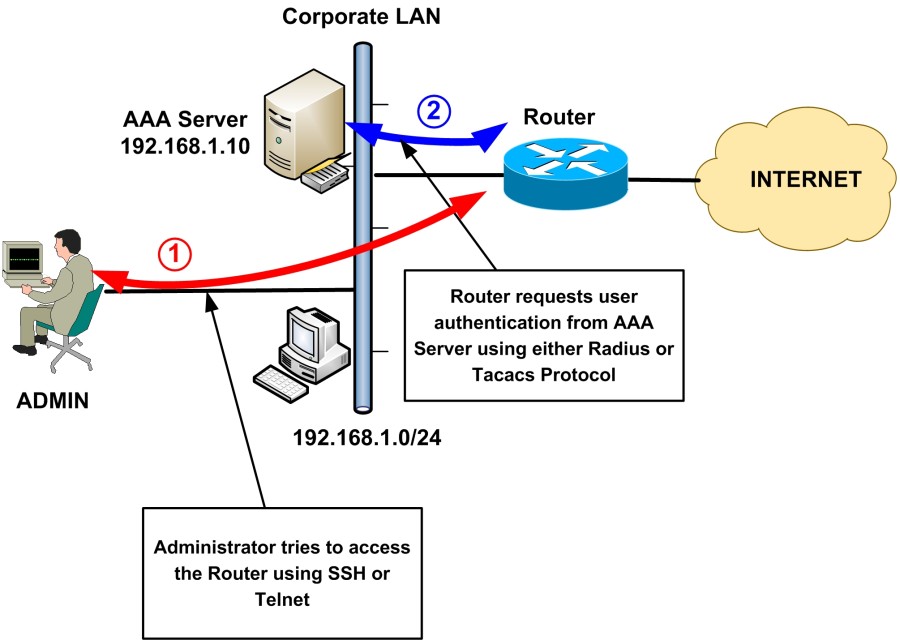
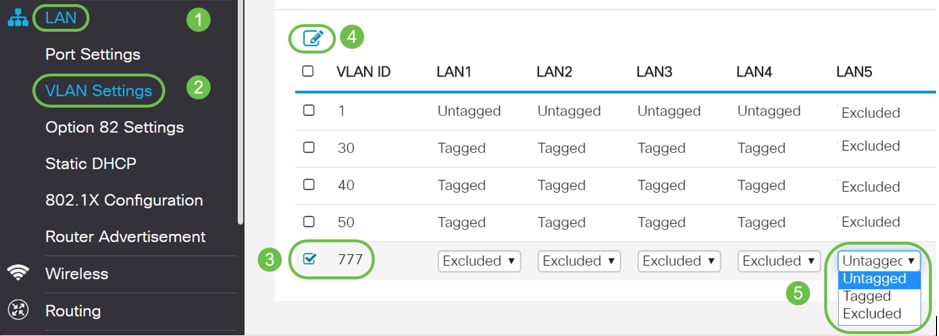
Objectives Upon completion of this module, you will be able to perform the following tasks: Describe the features and functionality of the Cisco Low End. - ppt download

Vulnerabilities in Cisco Small Business routers could allow unauthenticated attackers persistent access to internal networks | The Daily Swig

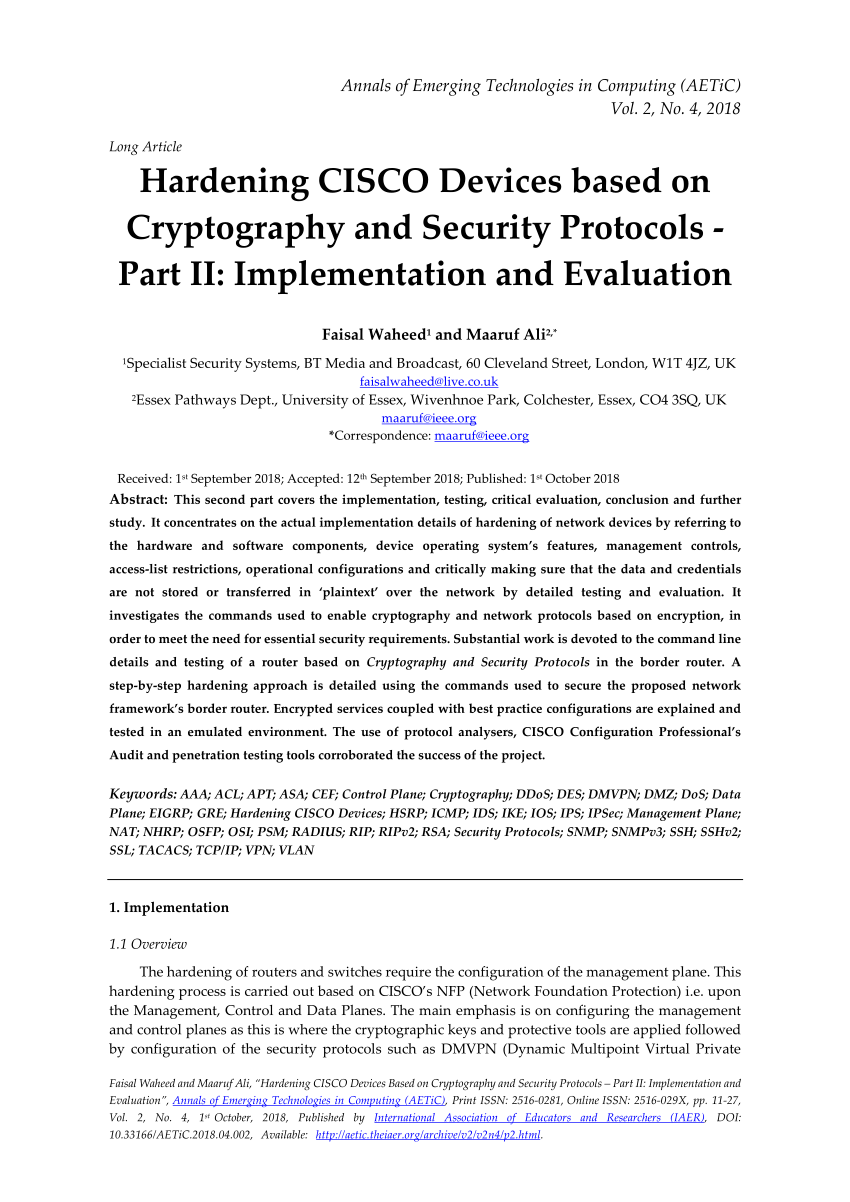
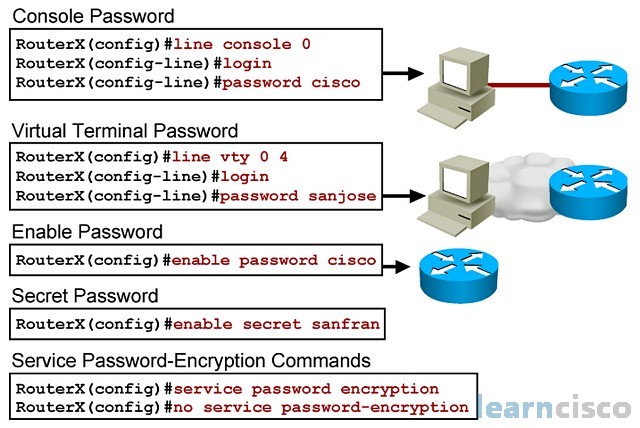
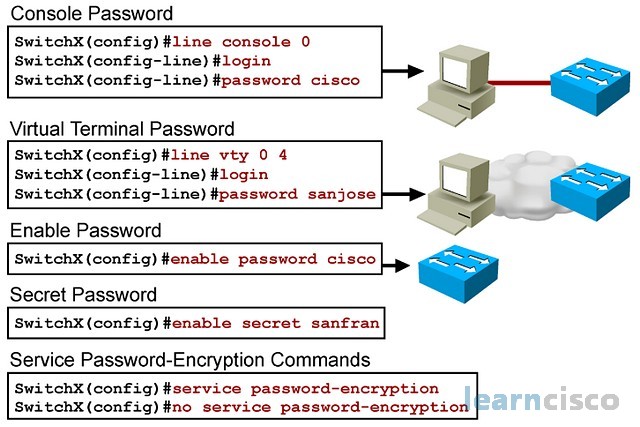
Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press